By Jürgen Backhaus, Senior BI Consultant at Stellar
By Jürgen Backhaus, Senior BI Consultant at Stellar
In our modern lives we are surrounded by technology almost all the time. Grabbing our mobile phone to check emails, scan social media or search for something on the internet is as normal as grabbing a glass of water.
Not so long ago, when we wanted to find out about a subject that we had read about or seen on TV, we had to get the encyclopedia and search for it, or even go to the library. Lots of younger people probably find this hard to imagine!
We still sit around the TV most evenings but often the TV is not getting our undivided attention because the smartphone or tablet is part of the entertainment.
We have embraced these devices and what they offer, without actually worrying about it.
I’m not talking about reduced communication between people in the same room. Rather, I’m referring to the fact that whatever we do on our devices leaves a trace.
Step by step, more devices are being introduced which can track our daily lives – often without us even being aware of it. Less obvious than laptops, tablets or smartphones, we now have intelligent fridges, intelligent home assistants and trendy wearable technology like smart watches and fitness trackers.
Don’t get me wrong, I am happily using some of these myself and they can make our lives easier and better. But there are also risks that this omnipresent technology could be used to control and harm us in ways which we cannot fully imagine.
 The situation described by George Orwell in his novel Nineteen Eighty-Four was a few years late arriving. When Orwell was writing, in the 1940s, surveillance was strictly analogue – but now it is digital and so much easier to record and access.
The situation described by George Orwell in his novel Nineteen Eighty-Four was a few years late arriving. When Orwell was writing, in the 1940s, surveillance was strictly analogue – but now it is digital and so much easier to record and access.
Are we OK with the level of surveillance in our lives today? And are we actually contributing to it by publishing on social media the things that used to be confined to diaries and family photo albums?
And what next? Are we willing to accept having even more information about ourselves uploaded to the vast data galaxy that we call the Internet of Things?
What is the Internet of Things?
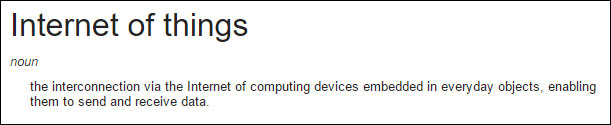
Arguably, all connected devices – including our computers, tables and smartphones – are part of the Internet of Things. But the IoT encompasses many more devices. It typically refers to “computing devices embedded in everyday objects, enabling them to send and receive data”.
The fact that they are included in “everyday objects”, almost disguised from our eyes, is what might be worrying. How do we prevent unauthorised access to, or manipulation of these small and proliferating devices?
A lot of IoT devices available today have only basic security mechanisms, with probably the most common being user/password protection. Unfortunately, many IoT devices are factory-defaulted with easy-to-guess usernames and passwords – or these may even be part of documentation which is ironically available via the internet!
Changing default passwords may not be easy for users who are actually tech-savvy. And in the case of “hidden” devices within an everyday object, the end-user might be completely dependent on the manufacturer to configure their security settings properly. Automatic updates of such devices and their settings are often not possible due to limited processing power.
An easy approach to fixing the default password would be to require the user to set up an individual password on first use of the device or to use passwords created by random number generators or based on unique characteristics of a device like the MAC address.
IoT risks in business
The above applies to personal use – but the risks are higher when IoT devices are used commercially as part of assembly lines, in public transport, power plants, hospitals, etc.
Assembly lines are already highly automated and packed with technology such as sensors, robots and terminals to monitor and control. The IoT brings greater control over production processes using new types of small and affordable sensors in places where they were not feasible previously.
Most importantly, it is possible to monitor and adjust the manufacturing process remotely, because all devices are connected by the IoT. Control is possible no matter whether their data is read and manipulated on a screen in the production plant or thousands of kilometres away on a smartphone while visiting a conference on the impacts of modern technology on the production process.
It is easy to imagine how sloppy security could allow production processes to be sabotaged, damaging the reputation of a company when it delivers low-quality products or cannot fulfil its delivery obligations.
In a hospital, IoT technology could administer medicine exactly where and when it is needed because specific sensors monitor the patient’s vital signs and connect to medicine dispensers. This could occur when the doctor gets a notification on her tablet, or even automatically. On the other hand, it is again easy to imagine that if someone with sinister motives gets access to the same devices they could use them to harm a patient, without even having to be in the same building.
Or consider the food industry, where a malicious change in a recipe could be harmful to consumers.
Admittedly, some of this technology is in its infancy or just an idea at this stage. And we all hope that when lives are at risk common sense will ensure there is advanced security on all devices involved.
Currently, many IoT devices are still seen as little more than “toys” and the danger is small, especially for the private user. But if an IoT application takes off, there will be inevitable pressure to mass produce it at low cost, possibly with weak security.
It seems more logical to improve the devices while people are still “playing” with them so that they are fit for purpose once the “serious” application starts.